Manage publicly exposed Postman API keys
Postman API keys provide access to the Postman user’s and team’s data. When Postman API keys are exposed in Postman public elements, such as public workspaces and documentation, as well as public GitHub and GitLab repositories, they are accessible to anyone on the internet—and this can be a nightmare for the user and team if they fall into the wrong hands.
Today, we’re announcing new capabilities to our Manage Postman Keys page, adding visibility and control for publicly exposed Postman keys.
Now, the Super Admin and Admin users in Postman can view publicly exposed API keys by visiting the Manage Postman keys page. Postman API keys detected in public repositories on GitHub and GitLab (only Ultimate projects supported on GitLab.com) and Postman’s public workspaces are visible on this page. Admins can see the name of an exposed key, location of the exposed key, the detected date, the last used date of the key, and the team member who created it.
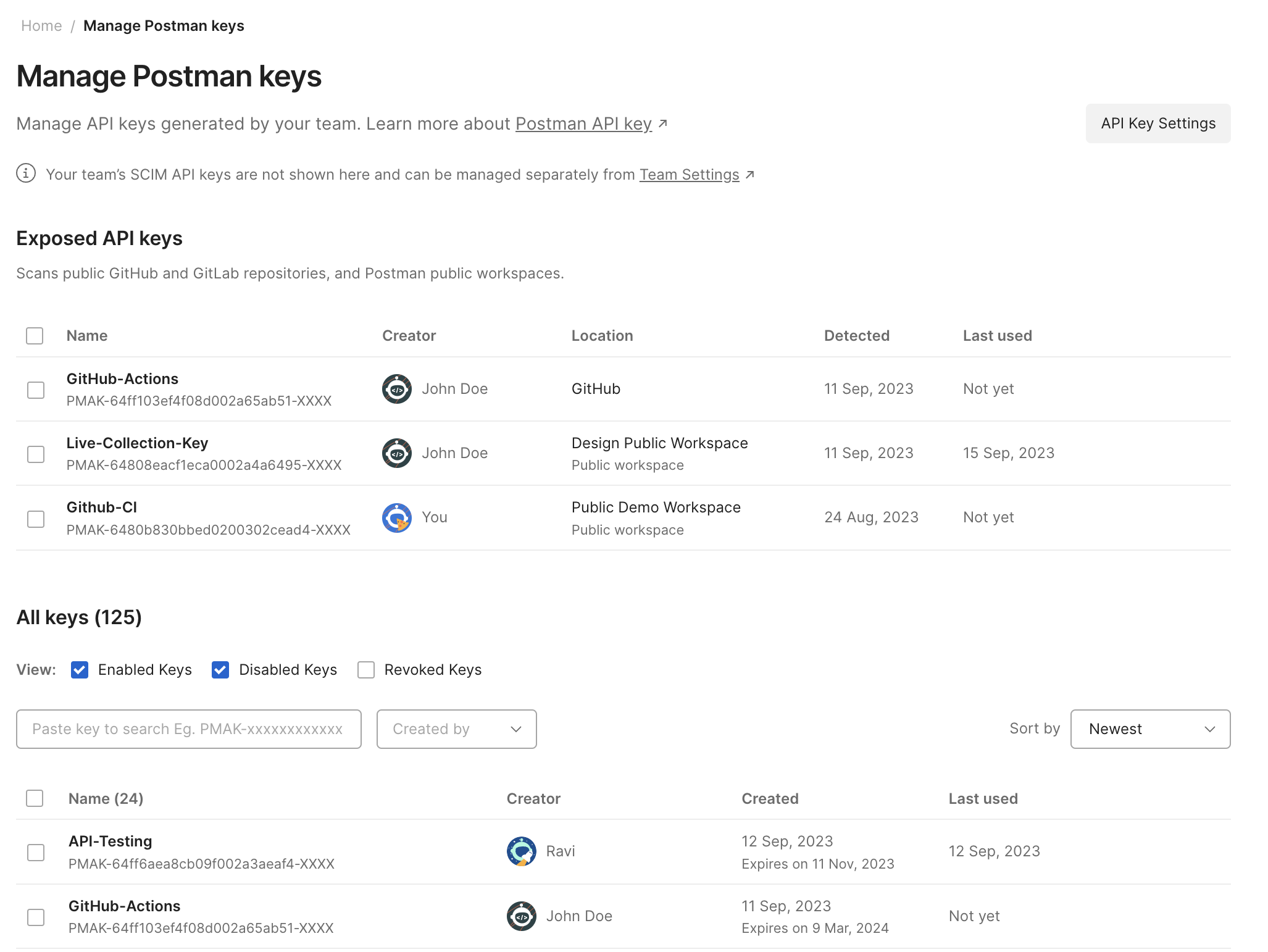
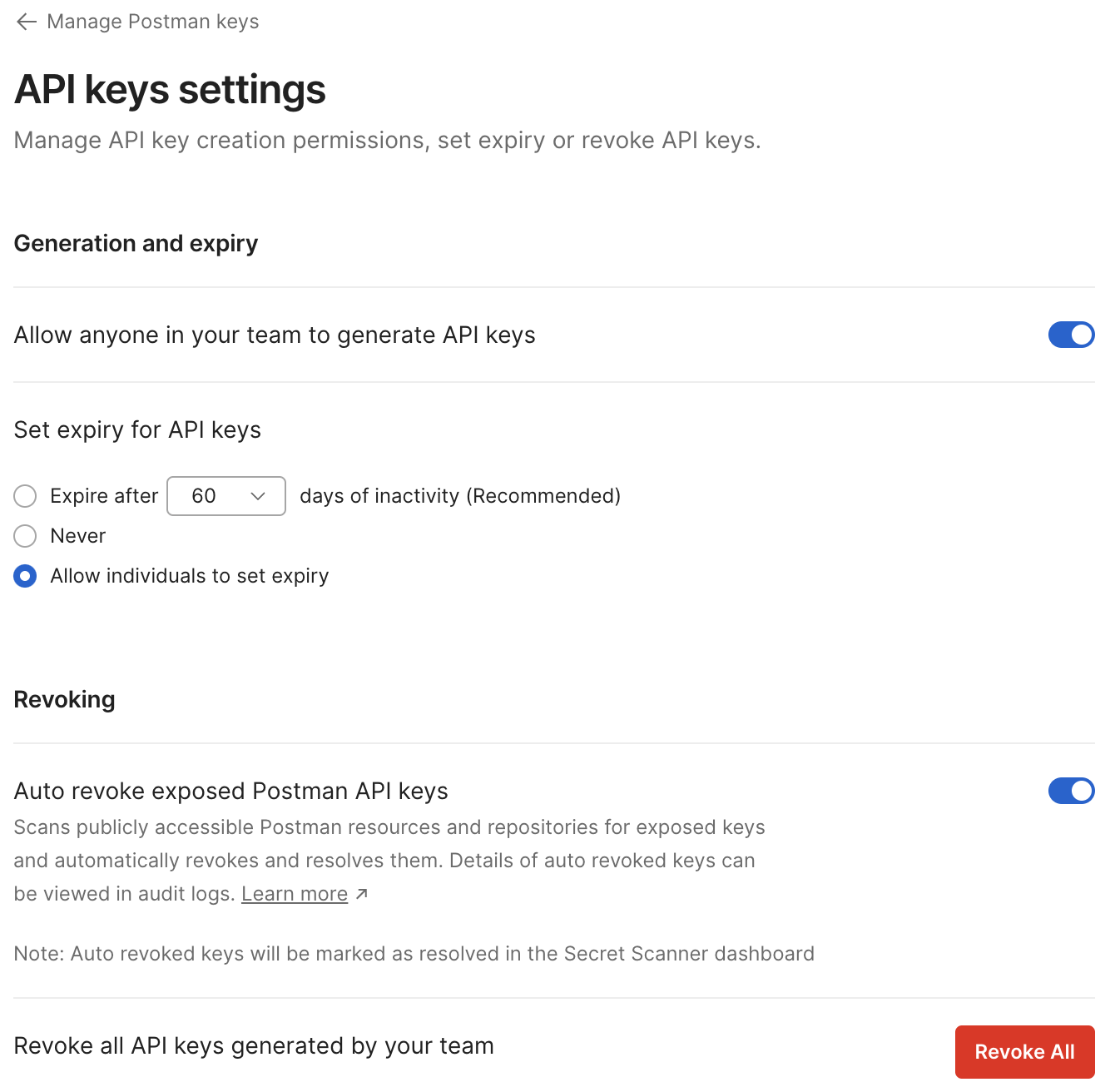
Super Admin and Admin users can revoke the exposed keys manually or by enabling a setting to automatically revoke a Postman API key when they are found to be exposed and notify the key owner via email. Admins can see all API keys revoked or auto-revoked on the Audit Logs page. Once a key is revoked, it will automatically resolve the corresponding finding on the Secret Scanner dashboard.
Learn more
This new feature that auto-revokes exposed Postman API keys is now available with all our Enterprise plans, so please get in touch with Postman sales to upgrade and gain access if you aren’t already an Enterprise plan user. You can also find more details about managing Postman API keys in our Learning Center. Additionally, you can visit the Postman Trust Center to gain knowledge about organizational security and how to protect your accounts and data in Postman.

It’s somewhat frustrating that the Postman team is signalling an interest in avoiding API secrets being exposed, and yet the September update requires the use of a Postman account, greatly increasing the risk that secrets in variables get synced with Postman’s servers.
I’m sure you have your business motivations for this, but this is not compatible with enterprise security policies so has forced us to migrate away. The recent use of hostile UX practices to trick users to creating online accounts has suggested that this change was coming, so although it is not a surprise, it is disappointing.