Introducing Postman Security Scans
According to the 2020 State of the API Report, businesses worldwide are becoming more reliant on APIs for their day-to-day work. And with the increasing number of APIs made available for public consumption today, it’s extremely important that any linked API documentation and saved examples demonstrating how to use an API don’t contain sensitive information that cybercriminals can exploit to gain access to private data.
When sensitive information is leaked to the public (i.e, through public documentation or through the contents of a public workspace), it can be detrimental to a user’s security posture and open up avenues that compromise the integrity of their data.
Postman is committed to providing users with the right tools to empower API development—and this includes efforts to make them aware of potential ways attackers can gain unwarranted access to APIs and services that we depend on.
The new Postman Security Scanner
To help better secure users, Postman has now added a Postman Security Scanner. With this new feature, a security scan is triggered whenever you do any of the following:
- Author new documentation for a Postman Collection and make it public
- Make any changes to a publicly available Postman documentation
- Change the visibility of a workspace to “Public”
- Share a collection or environment to an already existing public workspace
- Make a change to a collection or environment that is present in a public workspace
As part of the security scan, the Postman Security Scanner checks all information that has been made public through Postman documentation or Postman collections and environments (via a public workspace) against these 14 types of sensitive tokens:
- Basic Auth
- Bearer Token
- Google API Key
- Google OAuth Token
- PGP Private Key
- Postman API Key
- RSA Private Key
- Slack Access Token
- Slack Webhook URL
- SSH (DSA) Private Key
- SSH (EC) Private Key
- SSH (OpenSSH) Private Key
- Stripe Restricted Key
- Stripe Secret Key
The new security scanner is enabled by default for all Postman users. If it identifies any tokens belonging to the token types mentioned above, it sends an email with the results to the respective user who has initiated the accidental leak.
Note: Postman Security Scanner only scans publicly available data. It does not track or scan any private data belonging to teams or users.
Here is a sample email notification triggered by the Postman Security Scanner:
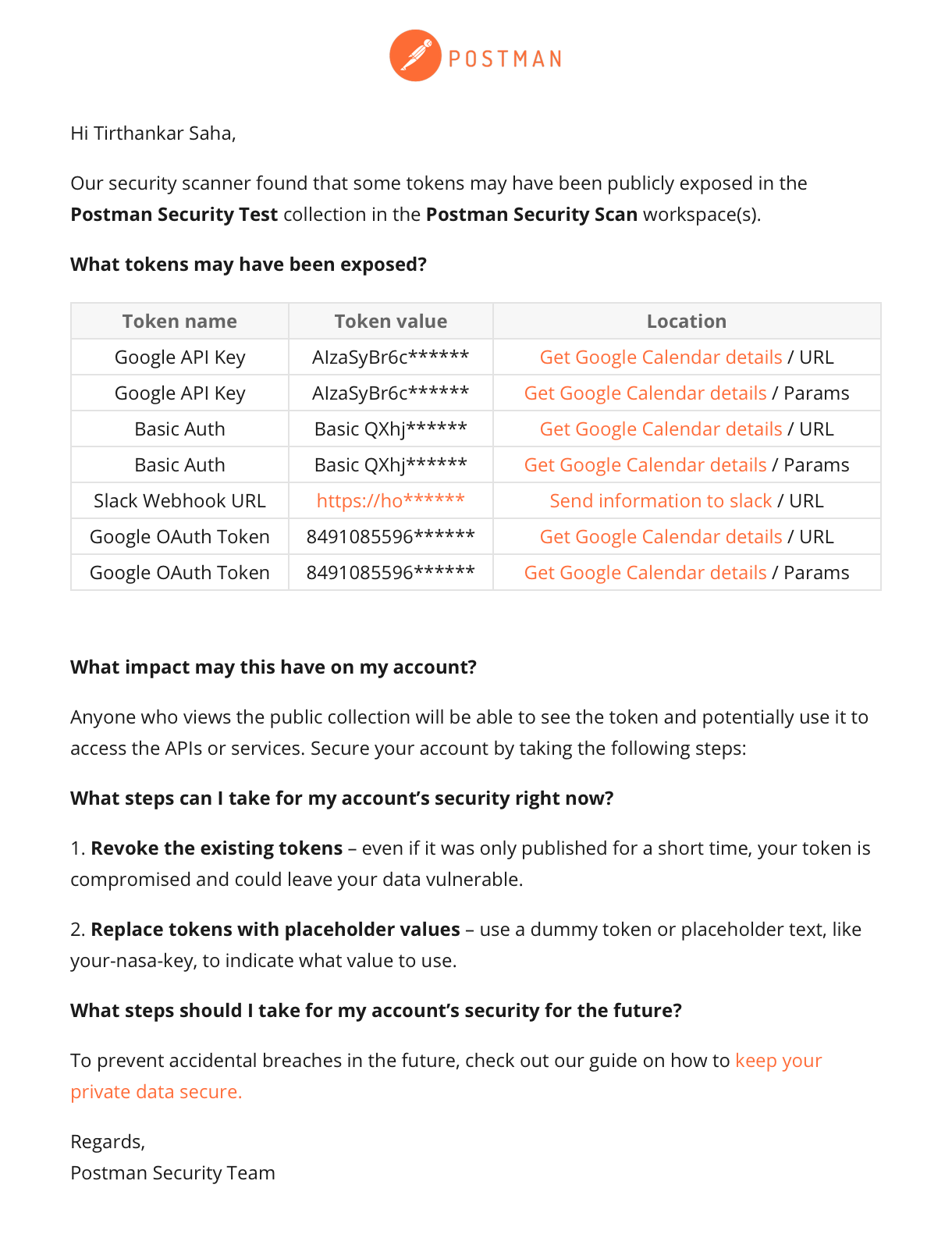
We’re constantly building new and better security features that can be leveraged throughout the API development lifecycle. Stay tuned for more updates as we plan to expand this initial list of tokens to further safeguard users against instances of excessive data exposure. Additionally, you can visit the Postman Trust Center to gain knowledge about organizational security and how to protect your accounts and data in Postman.
Technical review by Joshua Scott, Joyce Lin, and Suhas Gaikwad.
Kan je me helpen met de API in te stellen aub gr bert