Updates to the Postman Secret Scanner
In today’s fast-paced and interconnected world, we must prioritize data security to protect our sensitive information from potential threats. Here at Postman, we are dedicated to providing our customers with the best possible tools to safeguard their data, which is why we are constantly enhancing our Secret Scanner feature. In this blog post, we’ll explore our recent Secret Scanner improvements, such as support for public documentation in the dashboard and reports, dry runs against custom secret patterns, and summary emails that will keep you updated about the Secret Scanner’s findings.
Secrets in public documentation
With the latest release, the Secret Scanner can now identify secrets in team and public workspaces, as well as in public documentation in all workspace types. Public documentation can be published from any workspace—including personal workspaces, which we were not showing on the Secret Scanner dashboard before.
Secret scanning in public documentation works the same way as in public workspaces. Additionally, the user who published documentation with secrets will receive an email, as well as in-app and Slack notifications as per their notification configurations. Follow the steps below to access secrets in public documentation.
Navigate to the Secret Scanner
To access the Secret Scanner, choose the Secret Scanner option under Team Settings. This will take you to the Secret Scanner dashboard:
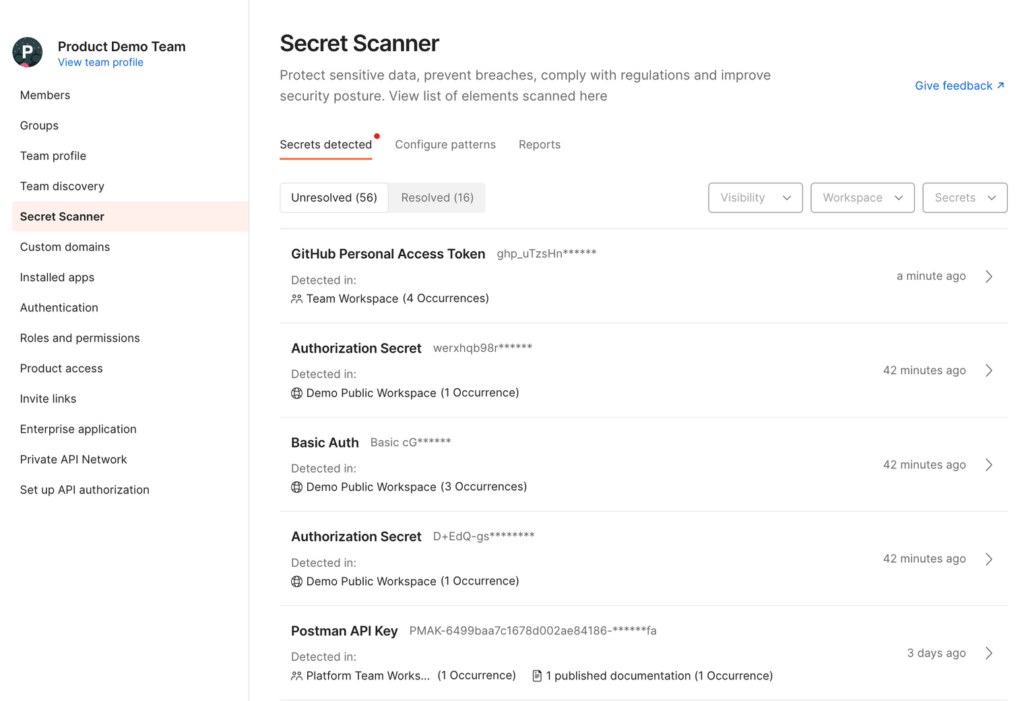
View secrets in public documentation
If the workspace’s visibility is set to “team” or “public,” we will display secret occurrences within that workspace, as well as within public documentation:
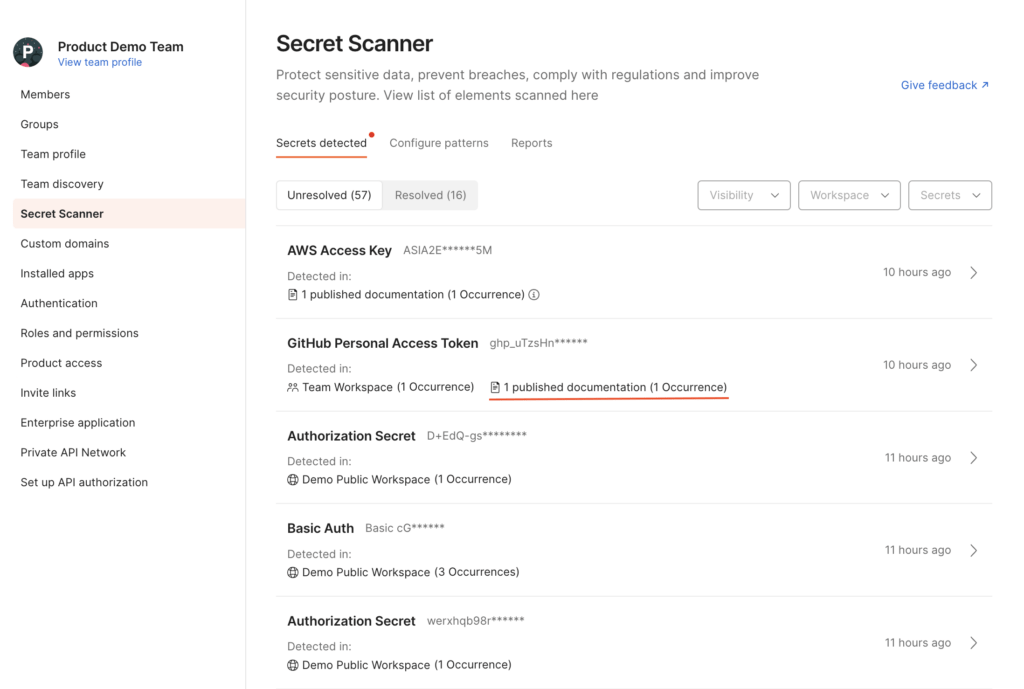
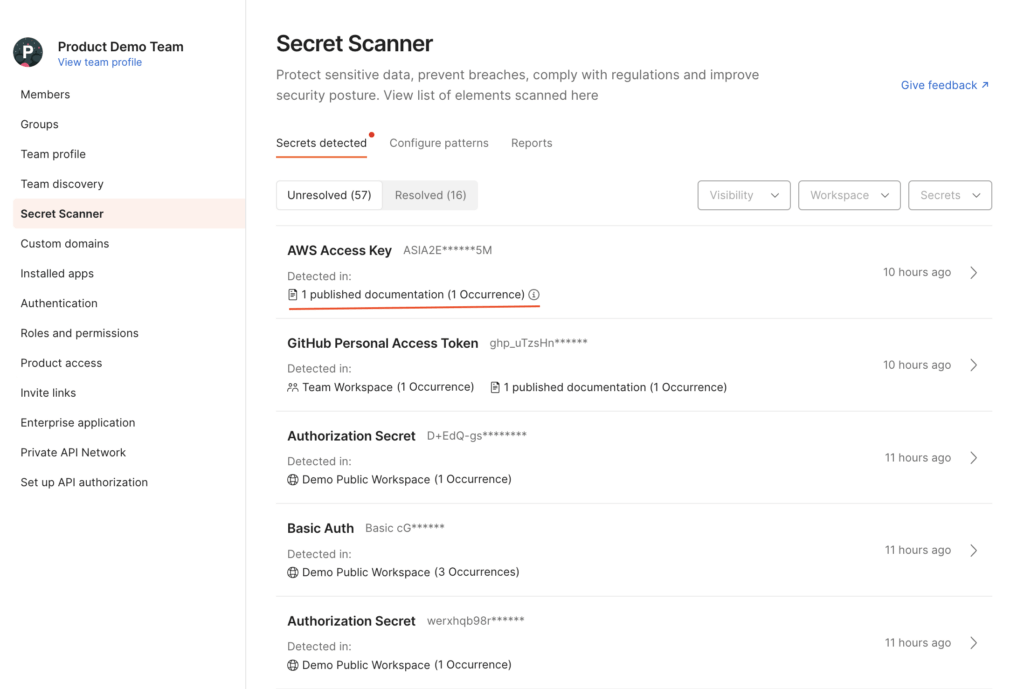
If the workspace type does not support secret scanning, as is the case with personal workspaces, the dashboard will only display secrets that are included in published documentation:
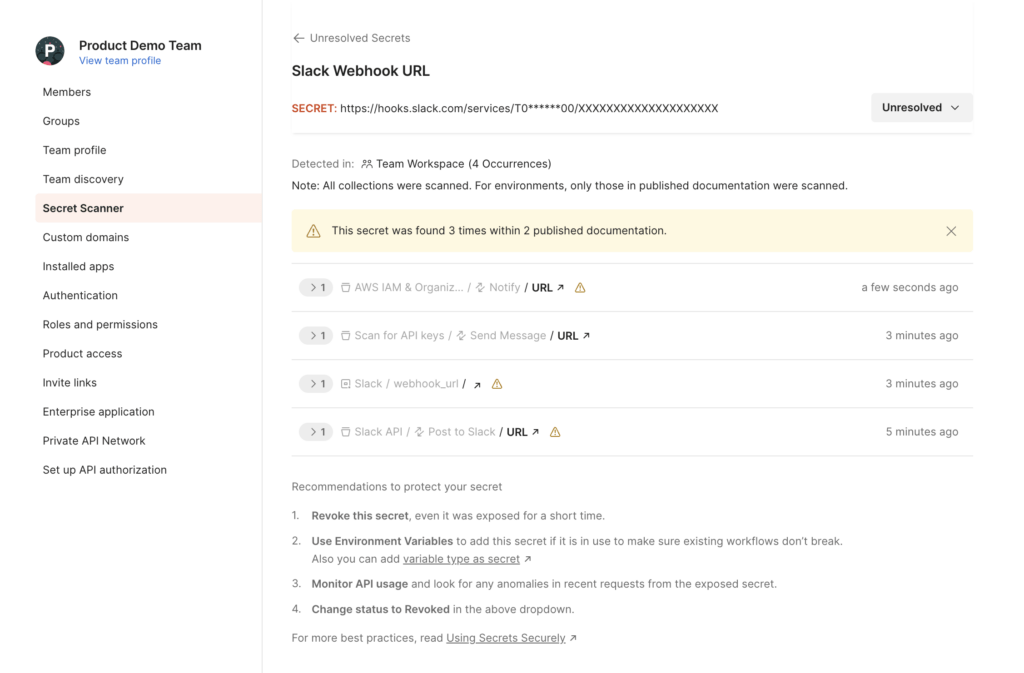
You can click on a secret to see more information about it, including recommendations to remediate the issue:
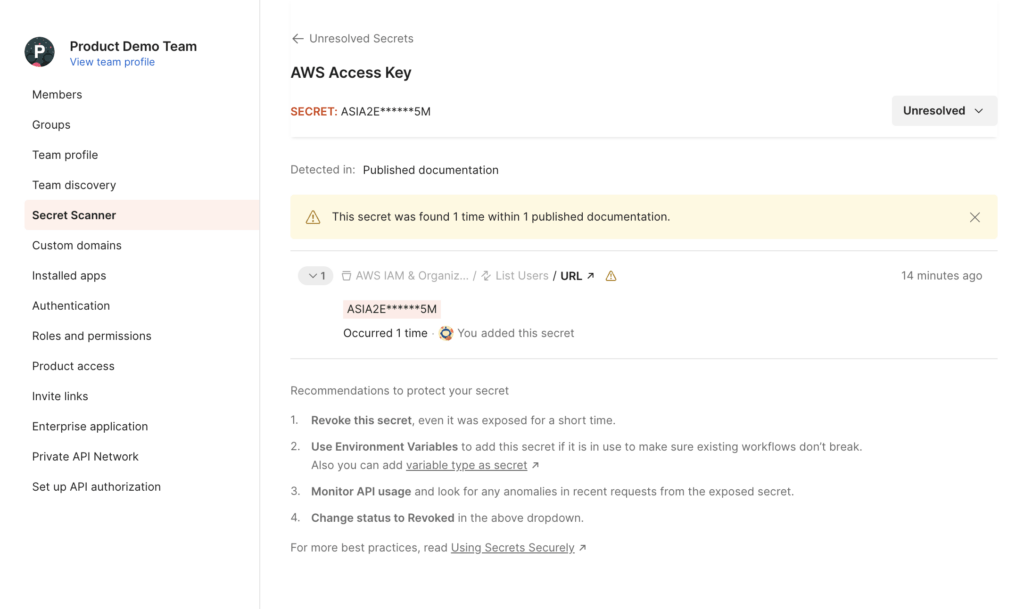
When there are multiple secrets with different visibility levels, as shown in the image below, a warning sign will highlight the ones that are public. This allows you to easily identify which resources are public and which are not. In a team workspace, secrets could be publicly accessible through collections or environments that were published as part of public documentation. Additionally, you have the ability to resolve findings for secrets that are present in public documentation.
Secret Scanner reports
We have made updates to the Secret Scanner report, which now includes secrets in public documentation. We have also added a new section called “Published documentation with unresolved secrets,” which lists the currently published documentation that contains unresolved secrets. You can access the updated report here.
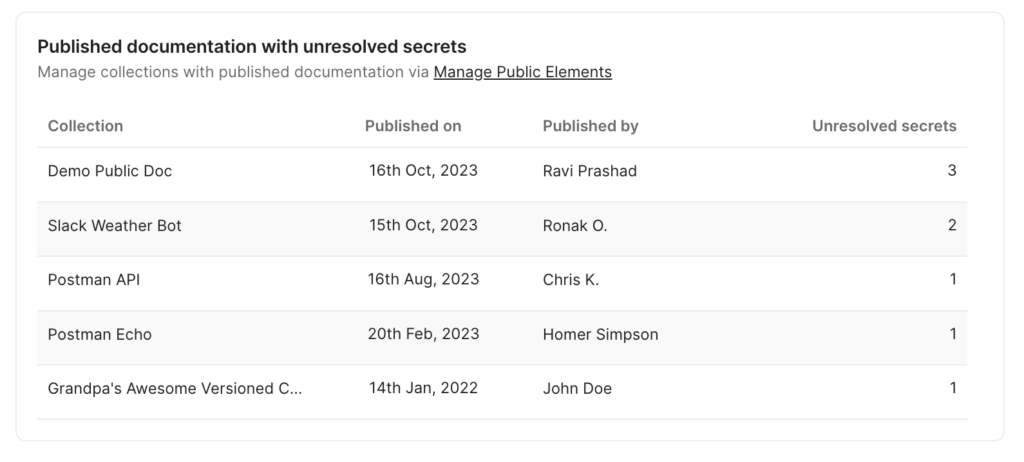
Clicking on the collection name allows you to access the public documentation. Additionally, the unresolved secrets count will redirect you to a page where detected secrets can be addressed.
Dry runs for custom patterns
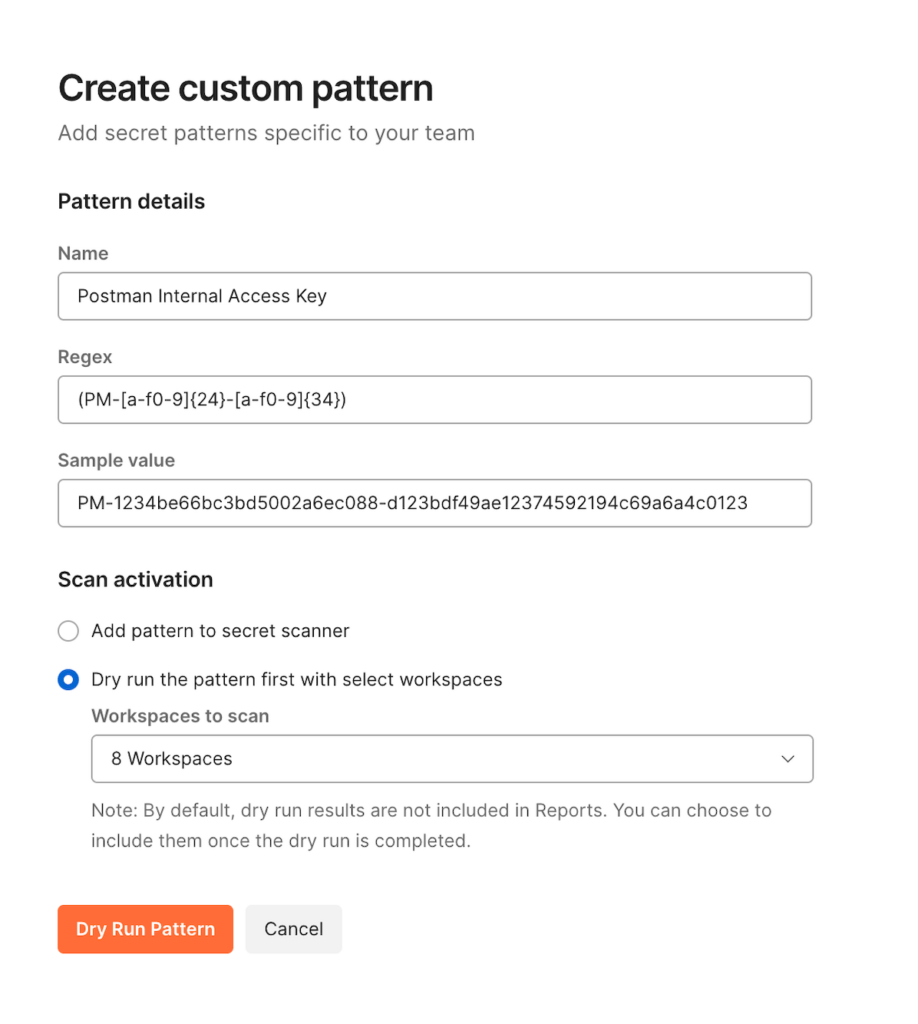
As an admin, you can set up custom patterns to monitor your team’s proprietary tokens, as well as any third-party app tokens that are not scanned by default. With this new release, you can now perform a dry run of your custom pattern at the team level. This will enable you to verify your custom pattern before publishing it to catch secrets.
You can add up to five custom patterns for the Secret Scanner by clicking the + button. To set up a custom pattern, you need to provide the following:
-
Name: The name of the custom pattern.
-
Regular expression: The regular expression that the Secret Scanner will use to identify the custom secret.
-
Sample token: A sample secret that you’d like to capture using this custom pattern.
-
Scan activation: To ensure that your custom patterns work as intended, you can use the scan activation setting to do a dry run before enabling them. Here, you have the option to choose existing elements to scan with your newly added custom pattern.
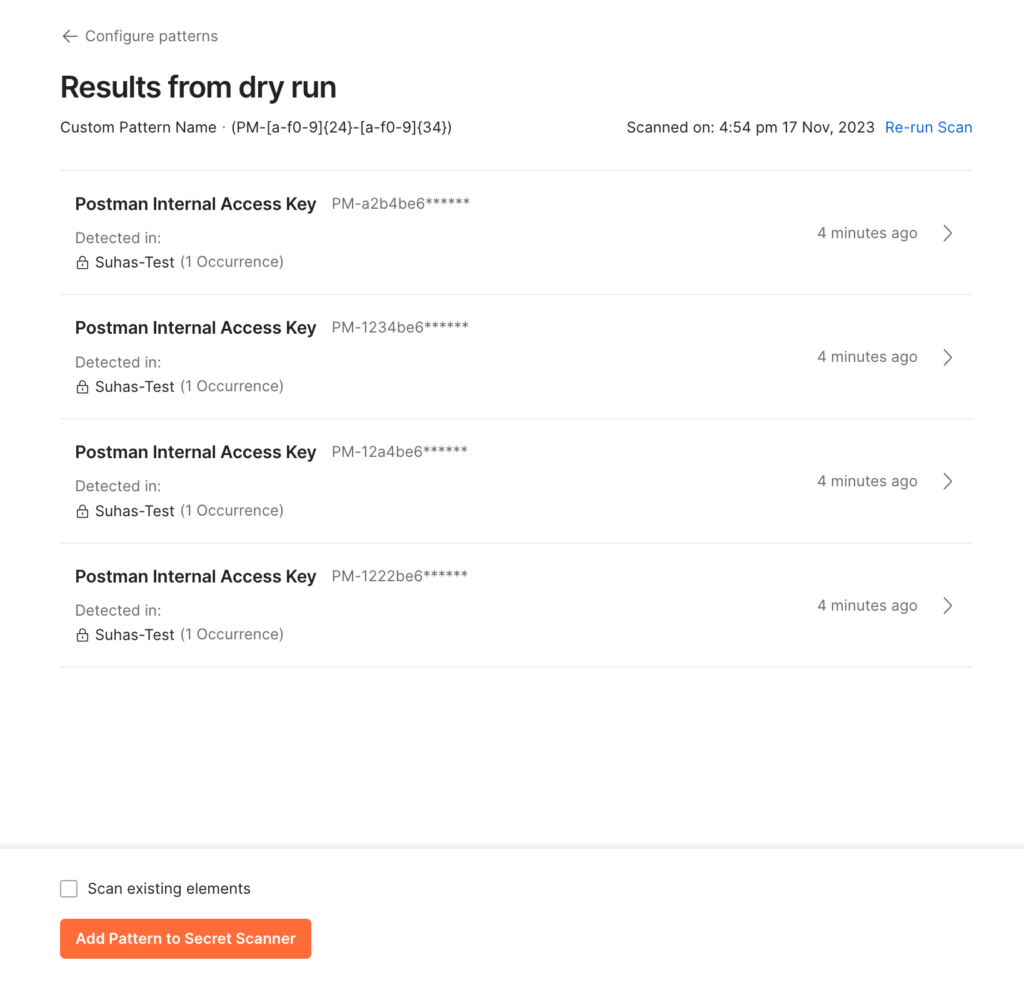
The dry run feature allows admins to run custom patterns on up to 20 workspaces. The results of the dry run scan are then presented to the admin for review. Based on the scan results, admins can choose to enable a custom pattern or make edits as needed. This feature provides an opportunity for admins to ensure that their alerts are working correctly before implementing them fully. Once you enable a custom pattern, the Secret Scanner will start scanning your custom pattern against your team’s Postman data.
Summary emails
Team admins, super admins, and workspace admins can stay informed about Secret Scanner findings by subscribing to weekly or monthly summary emails. These admins will receive a monthly summary email on the first of every month and a weekly summary email every Monday.
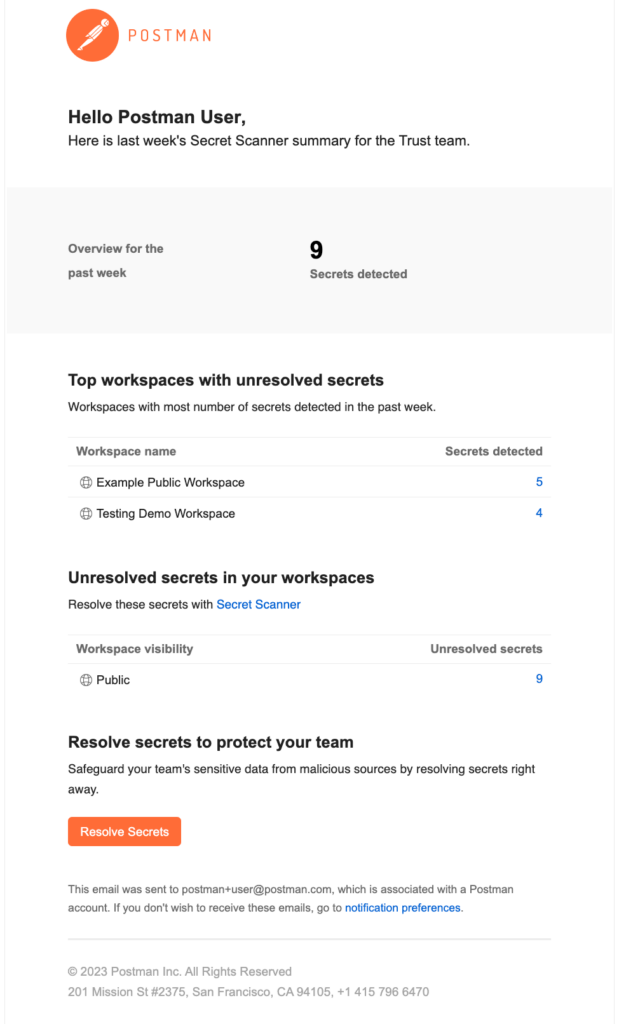
How do you subscribe to summary emails?
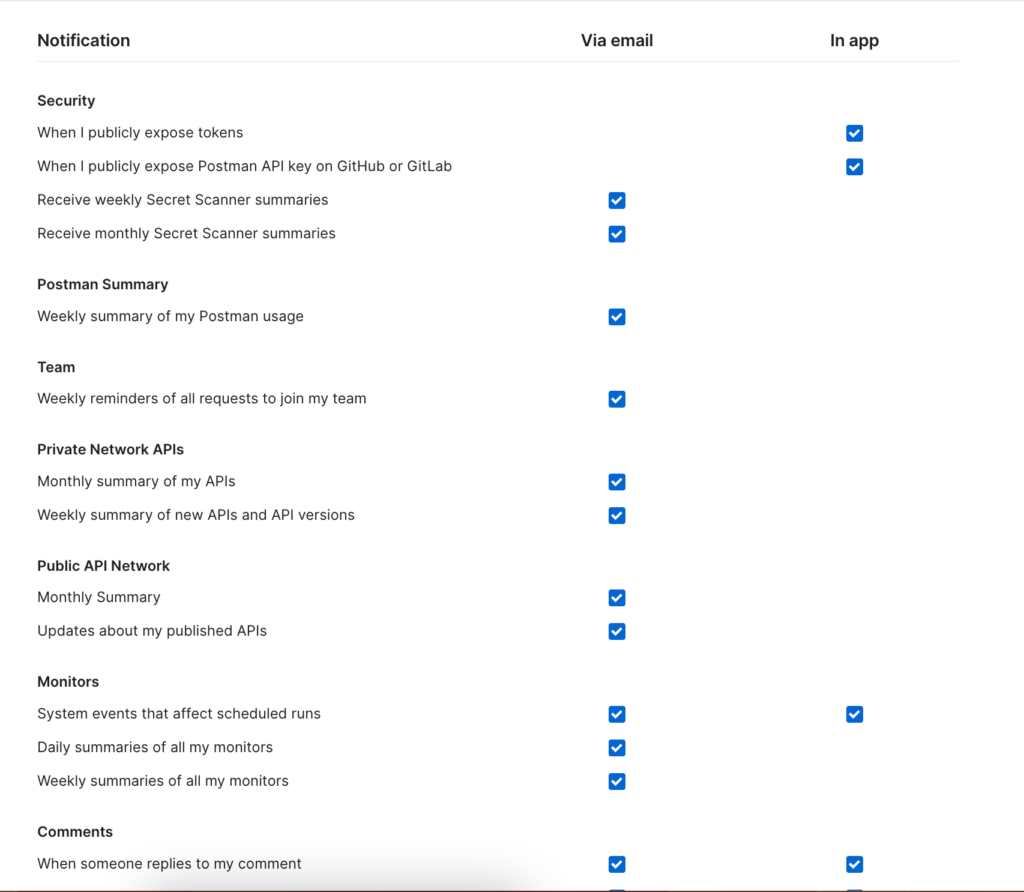
Navigate to Notification Preferences or select your avatar in the Postman header, then select Settings > Notifications to view the Secret Scanner summary option. From there, you can check the box for either weekly or monthly summaries—or both—and save your preferences:
Learn more
Learn more about the Secret Scanner in our Learning Center. Additionally, you can visit the Postman Trust Center to gain knowledge about organizational security and how to protect your accounts and data in Postman.

What do you think about this topic? Tell us in a comment below.