How we’re protecting your Postman API keys in GitLab
Today, we’re excited to announce a new integration with GitLab Secret Detection, which will protect your Postman API keys in GitLab public repositories. If you accidentally commit a valid Postman API key to a public repository on GitLab.com, this service will notify you. To activate this protection, enable GitLab Secret Detection in an Ultimate project on GitLab.com, which will enable you to respond quickly and help prevent any unauthorized access to your data in Postman.
How it works
Related: How to use API keys
GitLab Secret Detection scans your code commits for many types of secrets, including Postman API keys. If a Postman API key is found in a public repository on GitLab.com, GitLab notifies Postman. Postman then sends you an email notification (see an example below). If you receive this notification, we recommend that you delete any exposed Postman API keys immediately. Once a key is exposed in the public repository, it is considered compromised and could potentially put your data at risk. To continue using the Postman API, it is advised that you generate a new key from your account and update your client applications to use this new key.
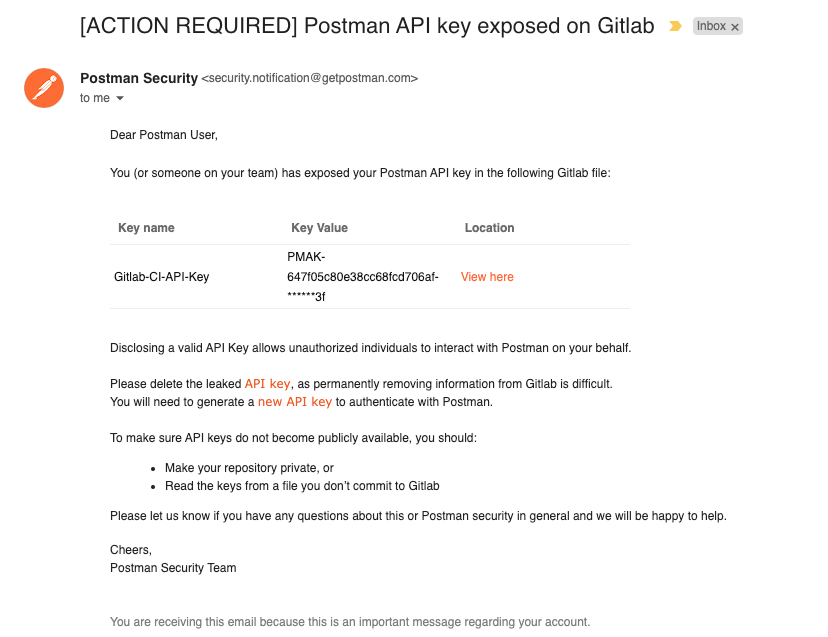
This feature is available to all Postman users and teams by default. It’s currently available in Ultimate projects on Gitlab.com that enable GitLab Secret Detection. We advise you to verify your email address with Postman to ensure that you receive these important security notifications. Also, don’t forget to visit our Postman Trust Center to learn about our organizational security and how to further protect your accounts and data in Postman.
What do you think about this topic? Tell us in a comment below.