Introducing Atlassian’s ASAP authentication in Postman
In the ever-evolving landscape of API development and testing, Postman aims to consistently ensure you have the right set of tools for your API needs. Authentication is one of the key areas in which we’ve seen our users face trouble, and we’ve been working hard to continuously improve our authentication landscape. In the last year, we’ve made well-received improvements, including token refresh support for OAuth 2.0, JWT auth, and even a simpler way to add auth to some of our public APIs.
Today, we are excited to announce support for Atlassian’s ASAP (Atlassian Service Authentication Protocol). It is a mechanism used by a resource server to authenticate requests from the client in a client-server communication scenario. ASAP uses familiar concepts for OAuth 2.0 and JWT, like client, resource server, access token, and more, with the goal of being performant and secure.
Getting started
Getting started using ASAP in Postman is pretty straightforward. You will find the ASAP auth list along with the other authentication protocols in the Authentication section in requests, folders, and collections. After selecting it, you’ll be required to fill in the essentials for creating a token, such as Algorithm, Issuer, Audience, etc. There is also a section for the optional fields, such as subject, additional claims, and expiry. With these details set, the token is created at runtime, i.e., at the time of request sending:
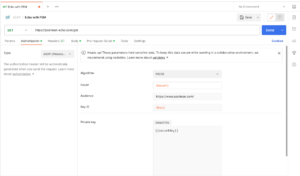
We really hope you like these changes. As always, we welcome your feedback in a comment below.
I tried using this in Postman 10.24.11 and was unsuccessful. It’s listed, I entered the data, and included the private key, but the token is never added to the request when I analyze it with Fiddler.
Please contact our support team at http://www.postman.com/support and they’ll be able to help you.